Latest News
New Ransomware Spreads Through Russia and Europe
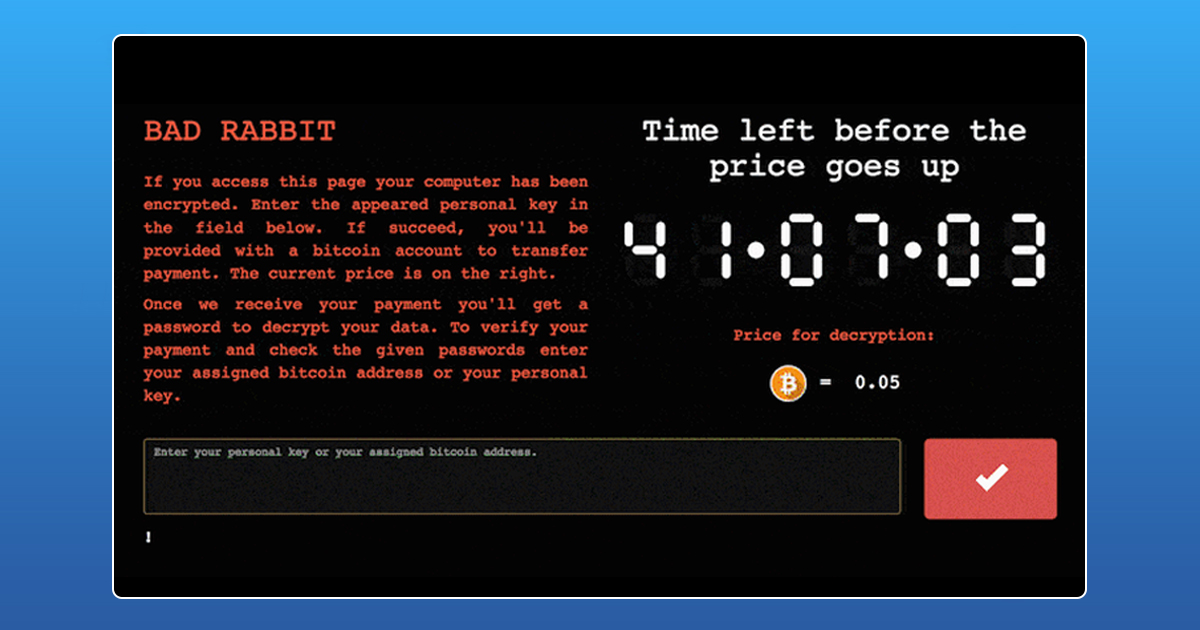
BadRabbit, a new ransomware, the next big cyber attack since ‘NotPetya,’ has been spreading across Russia, Ukraine and other Eastern European countries. Ukraine’s Computer Emergency Response Team (CERT) has confirmed the news regarding the new wave of hacks infecting computer systems in the country.
According to media reports, the ransomware is targeting corporate networks, computer systems for the Kiev Metro, Ukraine’s Odessa International Airport and several Russian media outlets. The malware has also reached Turkey and Bulgaria in addition to Germany and a few other countries. Currently, ESET and Kaspersky’s cybersecurity researchers are keeping a track of the attack.
According to ESET, the malware used for the cyber attack was Diskcoder.D, which is a new variant of ransomware also known as Petya. In June this year, the previous variant of Diskcoder, NotPetya, was used in a damaging cyber attack on a global scale. According to Wired, Kaspersky has counted close to 200 BadRabbit victims out of which 50 or 60 are Ukrainian government computers. However, ESET estimated only 12. 2% of victims were from Ukraine while 65% of the victims were in Russia.
Speaking about the latest cyber attack, Roman Boyarchuk, the Head of the Center for Cyber Protection in Ukraine said, “A lot of systems have been manually disconnected because of the attack, in part to control the spread of the ransomware.” While the outbreak has affected only a small fraction of the size of the NotPetya epidemic, Kaspersky found strong evidence tying the new attack to the creators of the NotPetya ransomware. The cybersecurity firm noted 30 sites which were used to spread Petya also began the distribution of the BadRabbit malware on Tuesday.
The Director of Kaspersky’s Global Research and Analysis team, Costin Raiu, said, “This indicates that the actors behind ExPetr/NotPetya have been carefully planning the BadRabbit attack since July.” The new ransomware, according to Kaspersky, spreads by using the Windows Management Instrumentation Command Line in combination with user credentials the malware steals using the open source tool Mimikatz. Similar to NotPetya, BadRabbit also uses Microsoft’s Server Message Block protocol to spread between computers, using the credentials hardcoded into its software.
Despite the various similarities, it’s still unclear who is behind the recent attack. All computers affected with the malware were directed to a .onion Tor domain and asked to pay 0.05 Bitcoins or roughly $ 276 in exchange for their data. However, all infected users are discouraged from paying the ransom as it is not yet clear if BadRabbit actually decrypts the data after collecting the ransom.
Latest News
₹290 Crore Boost: Rozana’s Series B Funding Scales Rural Retail Network Nationwide

Rozana, India’s leading rural retail platform, has secured ₹290 crore ($35 million) in a Series B funding round led by Bertelsmann India Investments (BII), with participation from Omidyar Network India, Vivid Capital, and Tana Investment Holding. This Rozana funding brings its total capital to over ₹500 crore, fueling hyperlocal expansion in underserved rural markets. Founded in 2021 by brothers Prashant and Prateek Chauhan, the startup’s phygital model blends micro-stores, app-based ordering, and last-mile delivery to connect 5 million+ users in 12 states with brands like ITC and HUL.
The ₹290 crore investment will supercharge Rozana’s rural omnichannel retail strategy, targeting 5x growth in 18 months. Plans include adding 5,000 micro-stores in Uttar Pradesh, Bihar, and Rajasthan; AI-powered inventory tech; and new categories like groceries and electronics. By empowering 20,000+ rural micro-entrepreneurs, Rozana taps into India’s $700 billion rural retail boom, where smartphone penetration and UPI drive 12% annual growth.
This Rozana Series B milestone positions it as a frontrunner against rivals like Ninjacart, eyeing unicorn status by 2028 amid ONDC tailwinds. CEO Prashant Chauhan emphasized, “We’re building rural prosperity through accessible premium brands.” For more on Rozana funding news and rural retail trends, stay updated on India’s startup ecosystem.
Latest News
Peak XV New Funds: $1.3B Commitment for India Startup Surge 2026

Peak XV Partners has launched three new funds totaling $1.3 billion, targeting India’s booming startup ecosystem. The lineup features the $600M Surge fund (8th edition) for early-stage ventures, a $300M Growth Fund for Series B+ scaling, and a $400M Acceleration Fund for rapid portfolio expansion. This commitment arrives as India’s VC inflows rebound, with AI and fintech leading 2026 trends.
These funds build on Peak XV’s legacy of backing unicorns like Zomato and Pine Labs, offering founders capital plus strategic guidance amid post-winter recovery. Early-stage deals surged 20% last year per Tracxn, positioning Peak XV to fuel the next wave of innovation in SaaS, climate tech, and consumer plays.
For startups eyeing Peak XV new funds or Surge fund 2026 applications, this signals prime opportunities. Investors and marketers should watch for deployment updates India remains a global VC hotspot.
Latest News
D2C Brand Neeman’s Raises $4 Million for Tier 2/3 Store Expansion & Eco-Friendly Shoes

Hyderabad, January 13, 2026 Neeman’s, India’s leading D2C footwear brand famed for sustainable shoes and patented PIXLL® technology, has raised $4 million from existing investors. This funding boosts its cumulative capital past $10 million since 2015, with a post-money valuation nearing $50 million. CEO Vijay Chahoria emphasized offline retail as the “next frontier,” planning 50+ new stores in Tier 2/3 cities like Jaipur and Lucknow to blend eco-friendly innovation with hands-on customer experiences.
In India’s booming D2C ecosystem where footwear sales hit ₹1.2 lakh crore in 2025 Neeman’s targets hybrid retail amid high online CAC and 25-30% returns. Backed by vegan, machine-washable shoes priced ₹2,000-4,000, the brand leverages PIXLL® (5x more breathable than leather) for carbon-neutral comfort. Recent 5x revenue growth to ₹100 crore ARR, 1M+ pairs sold via Myntra and stores, and awards at India D2C Summit 2025 position it ahead of rivals like Paaduks.
Neeman’s offline expansion India eyes the $15B sustainable footwear market by 2028, fueled by PLI schemes, Gen Z’s 70% eco-preference (Nielsen), and Southeast Asia exports. Challenges like real estate costs are offset by data-driven inventory and omnichannel QR tech. Watch for Q1 2026 launches in Hyderabad and Bengaluru redefining D2C success through authentic, “Wear the Change” branding.














Uduidbgf
May 26, 2025 at 5:39 pm
Explore the ranked best online casinos of 2025. Compare bonuses, game selections, and trustworthiness of top platforms for secure and rewarding gameplaycasino activities.
MM88
November 5, 2025 at 7:19 pm
Khám phá thế giới giải trí trực tuyến đỉnh cao tại MM88, nơi mang đến những trải nghiệm cá cược thể thao và casino sống động.
J88
November 7, 2025 at 7:04 am
Đến với J88, bạn sẽ được trải nghiệm dịch vụ cá cược chuyên nghiệp cùng hàng ngàn sự kiện khuyến mãi độc quyền.
iwin
November 10, 2025 at 7:02 am
iwin – nền tảng game bài đổi thưởng uy tín, nơi bạn có thể thử vận may và tận hưởng nhiều tựa game hấp
站群程序
November 11, 2025 at 6:07 am
采用高效谷歌站群策略,快速提升网站在搜索引擎中的可见性与权重。谷歌站群
谷歌站群
November 12, 2025 at 11:35 am
专业构建与管理谷歌站群网络,助力品牌实现全域流量的强势增长。谷歌站群
Kuwin
November 12, 2025 at 4:57 pm
kuwin sở hữu kho game đa dạng từ slot đến trò chơi bài đổi thưởng, mang đến cho bạn những giây phút giải trí tuyệt vời.
GO88
November 22, 2025 at 7:48 pm
Tham gia cộng đồng game thủ tại Go88 để trải nghiệm các trò chơi bài, poker phổ biến nhất hiện nay.